AWS KMS
AWS KMS is the service that amozon provided for managing encryption keys.
Before really dive into AWS KMS, it’s better to introduce several concepts about encryption. Generally there are two types of encryption, one is symmetric encryption another is asymmetric encryption.
Symmetric encryption is normally used for local file encryption, as the name indicates symmetric encryption uses one key to encrypt data and using same key to decrypt data, in such case keep this key secret is important.

symmetric
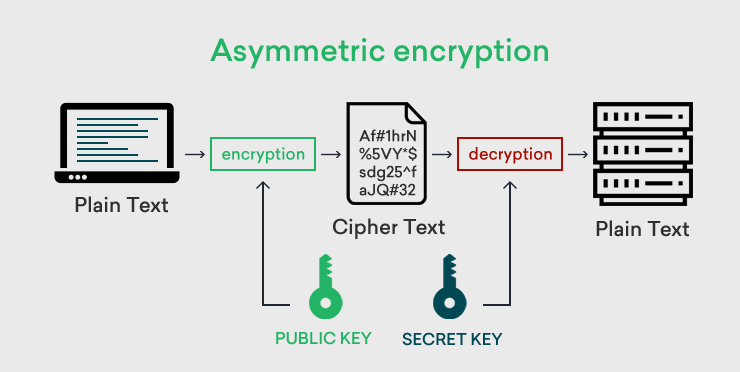
Asymmetric encryption is generally used for transmission scenario, for example keep a secret tunnel to transmit files. Asymmetric encryption has two keys. One key is called private key, another key is called public key. Private key will be always kept in the sender part and never revealed it publicly. Whereas, public key can be transmitted to worldwide. General use case is following
Step 1: sender will send his/her public key to receiver (actually anyone can have the public key).
Step 2: receiver is now able to use the public key to encrypt his/her data, then send back to the sender, even there is an eavesdropper, the eavesdropper cannot use his/her public key to decrypt this data. Therefore, data will be kept secret between the real sender and receiver.
Step 3: when sender gets the encrypt data package, sender uses his private key to decrypt the packge.
asymmetric
Both symmetric and Asymmetric encrytion are used for avoiding information leak to others. There is another important concept called digital signature is also worth to mention before give the detail of AWS KMS. Digital signature is used for keeping data integrity, avoiding data forge, notice it’s different than symmetric and asymmetric above, digital signature is not used to make data secret. However, digital signature utilizes asymmetric encryption. The way that digital signature works by following step.
Step 1: sender using certain hashing algorithm (md5 for example) to generate a data digest, this digest represents the data, even one byte change, the digest will be different.
Step 2: sender using his/her private key to encrypt the digest which can be decrypt by public key.
Step 3: when receiver gets the data and encryptd digest, receiver can decrypt the digest first, then using same hashing algorithm to hash the received data. Afterwards, comparing the generated digest with the received digest, if there is any difference, it means the data has changed by someone.
Notice, anyone who has the public key can decrypt the sender’s package. However, once they change any information inside the data and using their public key to encrypt the digest. The real receiver will not be able to use his public key to decrypt the encrypted digest, since public key cannot used to encrypt/decrypt data.

digital
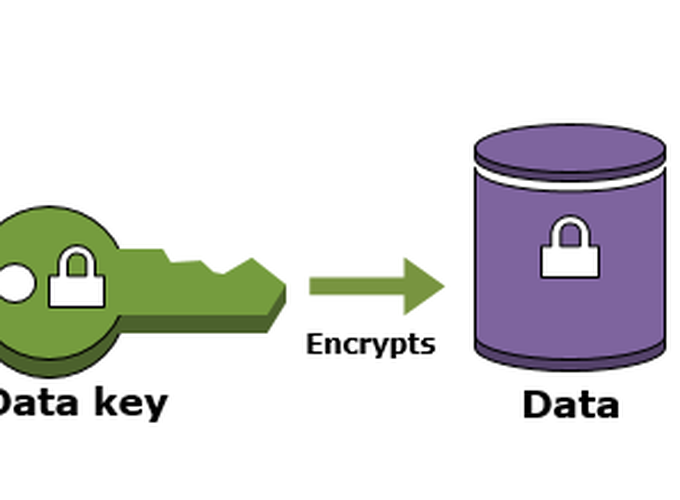
Now, it’s the right time to give the detail of AWS KMS. AWS KMS is used to manage symmetric keys, not asymmetric keys. AWS KMS uses a concept called envolope encryption, before introduce this concept, it’s better to understand two other things, one is called master key, another is called data key. Data key is the real encryption key that used to encrypt your data. Whereas, master is used to encrypt your data key, this process makes the encryption more strong. There is one more difference between data key and master key, you can view the data key but you cannot really view the master key, because the master is kept on AWS and managed by AWS, you can use but not view it. The process of envolope encryption is like this, AWS KMS generates data keys which used to encrypt client data, at the same time AWS KMS using master key to encrypt the data keys. Now you use the generated data keys (plain text) to encrypt data with the encrypted data key attached and the plain text data keys will be destroied. When clients want to decrypt the data, they have to use the master key to decrypt the encrypted data key first, after the data has been decrypted, clients can use the decrypted data key to decrypt the data [1].

kms
References
1. Escrowed data and the digital envelope.
Ables K, Ryan MD.
In: International conference on trust and trustworthy computing. Springer; 2010. pages 246–56.